Typical vulnerabilities
Causes behind vulnerability points
In most cases, we can read about a specific point of vulnerability and the specific method of attack in the media, but the reasons for the possibility of attacks are rarely mentioned.
Whatever IT-related changes we plan to make, regardless of headcount and company size, - based on the Compuquip team, - the following four weaknesses are worth considering:
- Network Vulnerabilities: These are issues with a network’s hardware or software that expose it to possible intrusion by an outside party. Examples include insecure Wi-Fi access points and poorly-configured firewalls.
- Operating System Vulnerabilities: These are vulnerabilities within a particular operating system that hackers may exploit to gain access to an asset the OS is installed on—or to cause damage. Examples include default superuser accounts that may exist in some OS installs and hidden backdoor programs.
- Human Vulnerabilities: The weakest link in many cybersecurity architectures is the human element. User errors can easily expose sensitive data, create exploitable access points for attackers, or disrupt systems.
- Process Vulnerabilities: Some vulnerabilities can be created by specific process controls (or a lack thereof). One example would be the use of weak passwords (which may also fall under human vulnerabilities).
Top 10 cyber security threats
A very understandable compilation from the Cyber magazine of ten of the top cyber security threats facing organisations today:
1. Ransomware attacks
Ransomware is a type of malware that prevents you from accessing your computer or the data that is stored on it. The computer itself may become locked, or the data on it might be stolen, deleted, or encrypted. The attacker will then demands a ransom from the victim to restore access to the data upon payment.
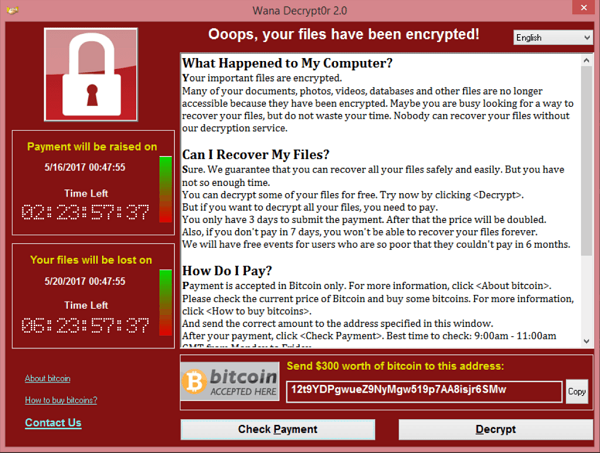
2. Cloud vulnerabilities
The more we rely on the cloud for data storage, the higher the risk of a major breach. Cloud services are vulnerable to a wide range of cyberattacks, but many businesses believe they are secure because they use cloud security technology.
In reality, technology is only part of the solution. Because no technology can completely eliminate vulnerabilities, a holistic approach is needed for robust protection. Insurance is an important piece of that protection as part of a comprehensive cyber risk management plan.
3. Phishing attacks
Phishing attacks continue to play a dominant role in the digital threat landscape. In its 2021 Data Breach Investigations Report (DBIR), Verizon Enterprise found phishing to be one of the most prevalent action varieties for the data breaches it analysed. Its researchers specifically observed phishing in more than a third (36%) of breaches. That’s up from 22% a year earlier.
4. Social engineering
Social engineering attacks exploit social interactions to gain access to valuable data. Cyber criminals trick and manipulate their targets into taking certain actions, such as bypassing security measures or disclosing certain sensitive information. Even the best cyber security systems can’t stop a social engineering attack, because the target lets the hacker into the system.
5. Patch management
Different relationships, even with the same vendor, expose an organisation to different levels of risk. Many retailers use third parties for services such as payment processing. Even if a company does not directly handle personal information—including social security numbers or credit card numbers—a third party can put them at risk. With malware, hackers can steal data through third-party vendors.
6. Internet of Things (IoT)
The Internet of Things (IoT) connects devices from all over the world through the internet. According to Deloitte, with the IoT, sensors collect, communicate, analyse, and act on information, offering new ways for technology, media and telecommunications businesses to create value—whether that’s creating entirely new businesses and revenue streams or delivering a more efficient experience for consumers.
Because of its convenience, many individuals and businesses are taking advantage of IoT, but the very thing that makes them convenient also makes them vulnerable. Hackers can exploit internet connectivity as an access point to steal data. As companies increasingly rely on IoT devices, many experts predict this will be one of the biggest cyber threats in the coming years.
A Fortune Business report indicates that the Internet of Things (IoT) market is likely to grow to $1.1 trillion by 2026.
7. Cryptojacking
Cryptojacking is a type of cybercrime that involves the unauthorised use of people's devices (computers, smartphones, tablets, or even servers) by cybercriminals to mine for cryptocurrency. Like many forms of cybercrime, the motive is profit, but unlike other threats, it is designed to stay completely hidden from the victim.
Mining for cryptocurrency requires immense amounts of computer processing power, therefore hackers make money by secretly piggybacking on someone else’s systems. For businesses, cryptojacked systems cause serious performance issues and costly downtime as IT teams track down and remove cryptojacking code.
8. Formjacking
Formjacking is a type of cyber attack where hackers inject malicious JavaScript code into a webpage form–most often a payment page form. When a site visitor enters their payment card information and hits submit, that malicious code collects the payment card number–as well as other information like the customer’s name, address, and phone number. The code then sends this information to another location of the attackers’ choosing.
In many cases, cybercriminals hijack the checkout page on eCommerce sites to steal financial information and credit card numbers. The goal is to skim valuable data submitted on the forms. Symantec’s Internet Security Threat Report shows formjacking dramatically increased. The report showed an average of 4,800 websites are compromised with formjacking code each month.
9. Third-Party Exposure
Many attacks start with outdated software. Not staying up-to-date with software patches can leave companies vulnerable to information security breaches and as soon as attackers learn of a software vulnerability, they can exploit it to launch a cyber attack.
Patch management is the process of distributing and applying updates to software. These patches are often necessary to correct errors (also referred to as “vulnerabilities” or “bugs”) in the software.
10. Endpoint Security
As more companies move resources into the cloud and rely on remote workstations, the attack surface increases. The challenge for organisations is how best to secure these off-premise systems and personal devices. Endpoint attacks are frequently used by cybercriminals to gain access to larger networks. By requiring endpoint devices to meet security standards before being granted network access, enterprises maintain greater control to effectively block cyber threats and attempts.
